
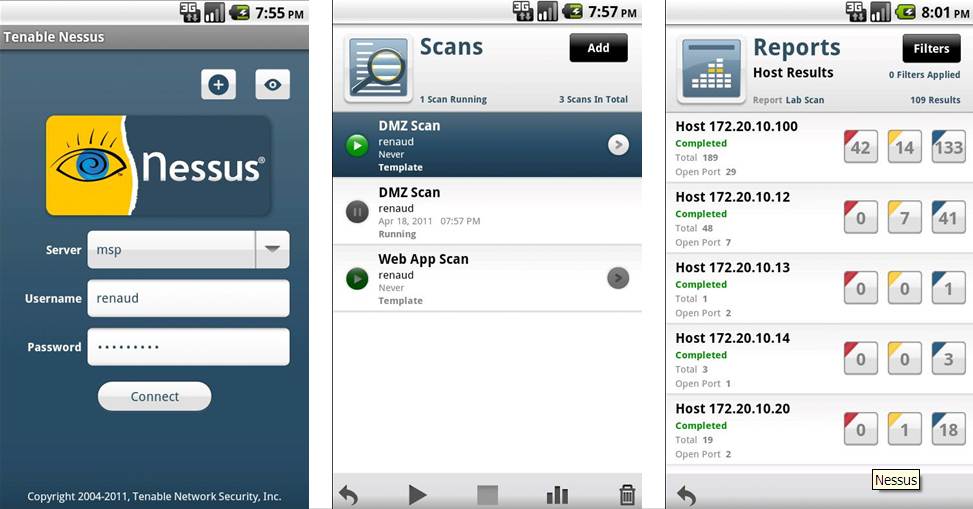
Nessus: A Comprehensive Guide to Vulnerability Scanning
Nessus is one of the most popular and widely used vulnerability scanning tools in the world. It helps organizations identify and fix security flaws in their network, systems, and applications. Nessus is highly effective in detecting vulnerabilities, misconfigurations, and weaknesses before they can be exploited by attackers. This blog will take a detailed look at Nessus, its features, uses, installation process, and how it helps in improving cybersecurity.
What is Nessus?
Nessus is a comprehensive vulnerability scanner that performs thorough network scans to identify potential security risks. Developed by Tenable, Nessus is available in both free and premium versions. The free version, called Nessus Essentials, offers limited features but is suitable for small networks or individuals looking to explore security scanning. The premium version, called Nessus Professional, offers advanced scanning capabilities and is ideal for businesses and security professionals.
Nessus checks for a wide variety of vulnerabilities including missing patches, weak passwords, unencrypted services, and common network vulnerabilities. It provides detailed reports, making it easier for security teams to prioritize and fix issues based on their severity.
Key Features of Nessus
Nessus provides a wide range of features that make it one of the top choices for vulnerability assessment. Some of its key features include:
Comprehensive Vulnerability Scanning: Nessus supports scanning for a wide range of vulnerabilities, such as missing patches, software flaws, misconfigurations, and other security risks in operating systems, applications, and network devices.
Customizable Scans: Nessus allows users to create customized scan templates based on specific needs. You can configure scans to target specific assets, protocols, or vulnerabilities, and schedule them to run automatically.
Integration with Other Tools: Nessus can integrate with various security tools such as SIEM (Security Information and Event Management) systems, ticketing systems, and other vulnerability management solutions. This makes it easier to manage and respond to discovered vulnerabilities.
Detailed Reports: After each scan, Nessus generates detailed reports that categorize vulnerabilities based on their severity (Critical, High, Medium, Low). It also provides remediation steps, making it easy to fix the identified vulnerabilities.
Compliance Checks: Nessus can be configured to check whether systems comply with various security standards and regulations, such as HIPAA, PCI-DSS, and CIS benchmarks. This helps businesses ensure that they meet industry-specific compliance requirements.
Advanced Authentication: Nessus supports both unauthenticated and authenticated scanning. With authenticated scanning, Nessus can log into systems with valid credentials to perform deeper, more accurate scans that go beyond what can be detected from the network.
How Does Nessus Work?
Nessus works by scanning the network and systems for known vulnerabilities using a process called network discovery. It uses a combination of plugins to check for specific vulnerabilities in the system. Nessus continuously updates its plugin database to stay up-to-date with the latest security flaws and threats.
- Discovery Phase: Nessus first discovers active devices and systems on the network. It identifies the operating systems, applications, and services running on each device.
- Vulnerability Detection: Nessus then runs checks against each discovered system to identify any security flaws. This is done through a series of tests such as port scanning, checking for outdated software, configuration flaws, and security loopholes.
- Reporting: Once the scan is complete, Nessus generates a detailed report that outlines all the discovered vulnerabilities. It provides a severity rating for each vulnerability and suggests remediation steps.
Types of Vulnerabilities Nessus Can Detect
Nessus can detect a wide variety of vulnerabilities, including:
Missing Patches and Updates: Nessus can check if systems are missing critical patches or updates that could leave them exposed to security vulnerabilities.
Misconfigurations: Systems and network devices may have misconfigurations that weaken their security. Nessus can detect common misconfigurations in firewalls, databases, and operating systems.
Weak Passwords: Nessus can check for weak passwords on devices and systems. It can perform brute-force attacks to identify weak or default passwords that may be vulnerable to exploitation.
Sensitive Data Exposure: Nessus can identify systems and applications that expose sensitive data, such as passwords, credit card numbers, or personal information, through insecure channels or in logs.
Unnecessary Services and Open Ports: Nessus can identify open ports and unnecessary services running on systems. These can be potential attack vectors that hackers can exploit to gain unauthorized access.
Web Application Vulnerabilities: Nessus includes checks for web application vulnerabilities such as SQL injection, cross-site scripting (XSS), and other common web-based security risks.
Installing Nessus
Nessus can be installed on Windows, Linux, and macOS systems. Here is a step-by-step guide to installing Nessus on a Linux system:
Download Nessus:
- Visit the Tenable website and download the appropriate version of Nessus for your operating system. You can choose between Nessus Essentials (free) or Nessus Professional (paid).
Install Nessus:
For Linux, open the terminal and run the following command to install the Nessus package:
bashsudo dpkg -i Nessus-<version>-ubuntu1110_amd64.debFor other operating systems, follow the installation instructions provided by Tenable.
Start Nessus:
After installation, start Nessus using the following command:
bashsudo systemctl start nessusd
Access Nessus Web Interface:
- Open a web browser and navigate to
https://localhost:8834to access the Nessus web interface. You will be prompted to create a user account and license key.
- Open a web browser and navigate to
Running a Nessus Scan
Once Nessus is installed and running, you can begin scanning your network for vulnerabilities. Here’s how to run a basic scan:
Log In: Log in to the Nessus web interface using your credentials.
Create a New Scan:
- Click on the “New Scan” button.
- Select the type of scan you want to run (e.g., Basic Network Scan).
- Configure the scan settings, including the IP range to be scanned.
Start the Scan:
- Click on the “Save” button to save your scan configuration, and then click on “Launch” to start the scan.
Review the Results: After the scan is complete, Nessus will provide a detailed report of the findings. You can view the vulnerabilities, their severity, and remediation recommendations.
Best Practices for Using Nessus
Regular Scanning: Conduct regular scans to identify vulnerabilities early and reduce the risk of an attack.
Prioritize Critical Vulnerabilities: Always focus on fixing critical vulnerabilities first, especially those that can lead to data breaches or unauthorized access.
Automate Scans: Use Nessus’ scheduling feature to automate vulnerability scans at regular intervals, so vulnerabilities can be identified without manual intervention.
Keep Plugins Updated: Nessus frequently releases plugin updates to detect newly discovered vulnerabilities. Regularly update your plugins to ensure your scans are up to date.



Zaproxy dolore alias impedit expedita quisquam.